This post will briefly compare and contrast the two most common authentication techniques: session-based and token-based authentication. Understanding the differences between these methods is crucial for selecting the right approach for your application’s needs.
Session-Based Authentication
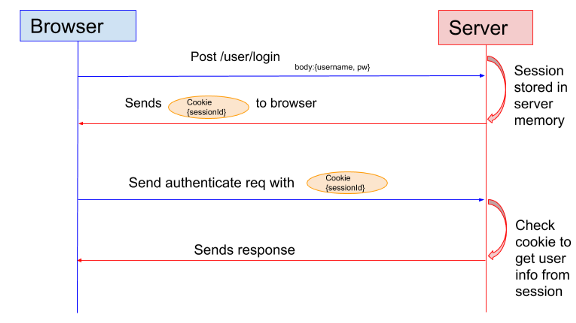
In session-based authentication, the server creates a session for the user after the user logs in. The server generates a session id that is stored in memory or an external cache for horizontal scaling. The client stores the session ID in a cookie and sends it in the request header for every subsequent request.
| |
The server can verify the user by comparing the session ID in the cookie against the session information stored in cache and respond accordingly.
Token-Based Authentication
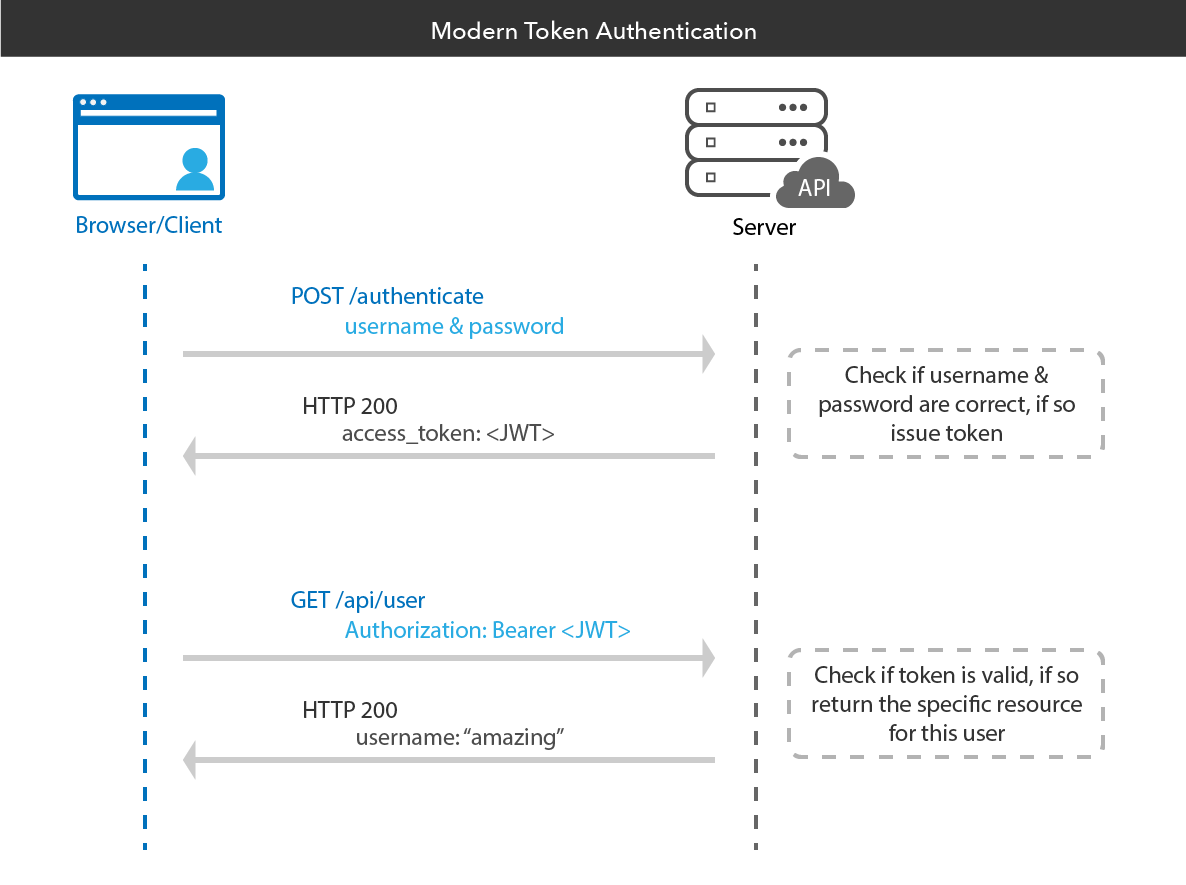
In token-based authentication, the server generates a JWT (JSON Web Token) with a secret and sends it to the client. The client stores the JWT in a cookie or local browser memory. Subsequent requests made to the server include the JWT in the header:
| |
The server validates the JWT to verify the user and respond accordingly.
Session vs. Token Authentication
Tokens (JWT)
- Can work cross-origin across different domains. Downstream services can share tokens.
- JWT-based authentication scales well horizontally because tokens are stored on the client side.
- Provides integrity protection using a signature or MAC.
Sessions
- Offers more control over sessions, as they are easier to invalidate. JWTs remain valid until their expiration date is reached.
- If a JWT contains a lot of data, it can slow down client requests. Session IDs are lightweight strings, making them more efficient. OAuth2 solves this issue by using short-lived access tokens and long-lived refresh tokens.
Conclusion
Most production services can work with either authentication model, so the choice depends on the use case. In fact, many systems use a hybrid model that combines both types of authentication, with the JWT being associated with a user session for user tracking.